Engage customers across the globe with confidence.

Thousands of businesses in more than 220 countries & territories trust Plivo’s cloud communications platform to simplify and personalize their customer communications, from APIs to solutions.




Thousands of large businesses globally use Plivo’s APIs












Top 3 Reasons Why Customers Choose Plivo

We’re not satisfied until you’re successful
Our consultative approach to engagement means we work with you every step of the way.

We build reliability into our platform
Behind the scenes, Plivo makes sure your communications get where they need to go every time.

Our complex applications are simple by design
We’re focused on keeping things simple for our users while allowing you to build complex applications.
It’s easy to get started — explore our products today!

Plivo CX
From personalized marketing campaigns to automated customer service, this all-in-one solution helps you attract, convert, and retain customers. Bring it all together with Plivo CX.
Learn More

Voice API
Use Plivo's Voice API to build AI-powered voice agents, create voice surveys, set-up automated alerts, conference bridges for team collaboration, and create intelligent IVR menus that route calls efficiently.
Learn More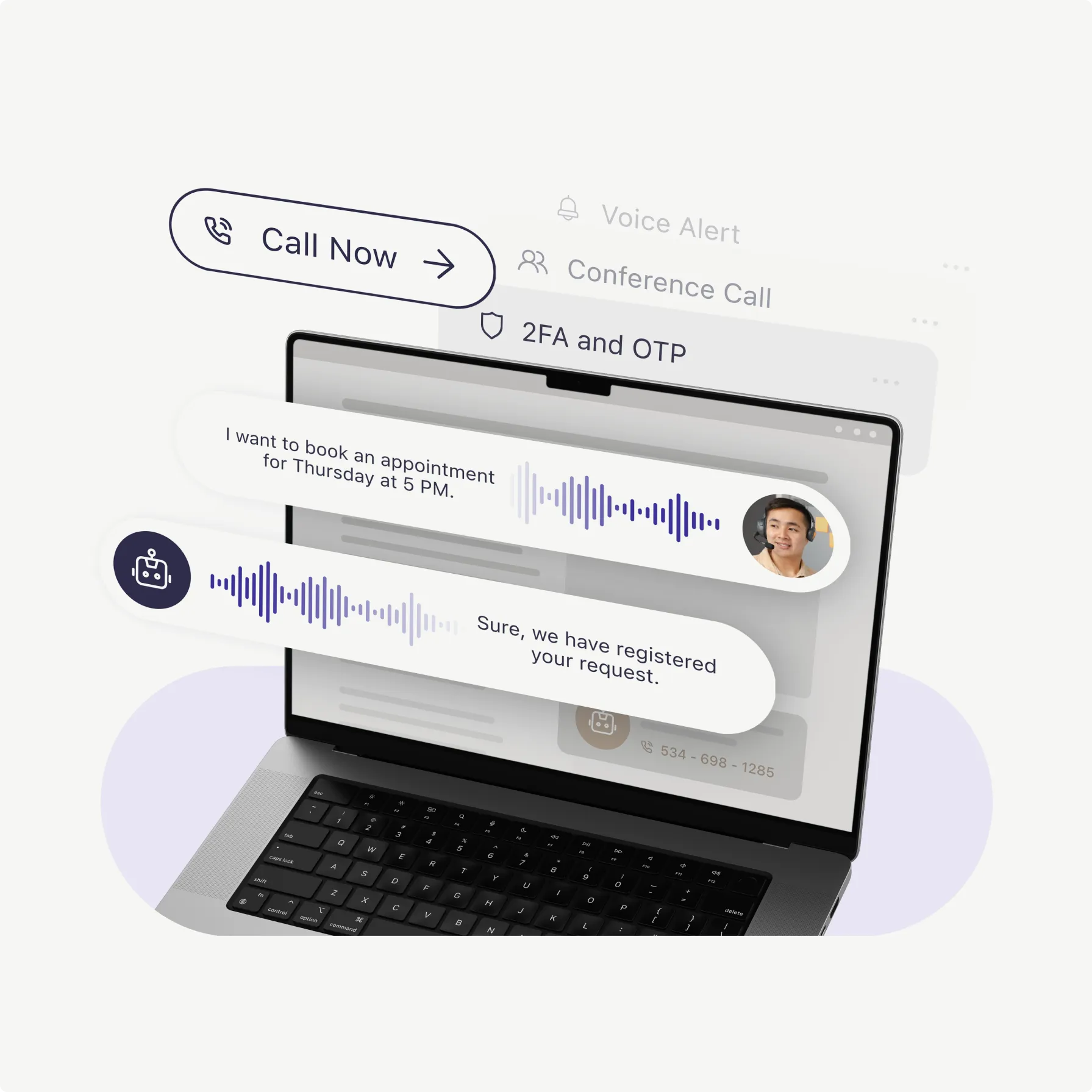

SMS API
Plivo’s SMS API allows businesses to send and receive text messages programmatically. Automate notifications, confirmations, reminders, and promotional messages directly from their applications.
Learn More

Verify API
Protect your platform with Plivo's Verify API. Deploy instant user verification across 150+ countries with industry-leading 95% conversion rates. Multi-channel support via SMS, Voice, and WhatsApp ensures you reach every user securely.
Learn More

Whatsapp Business API
Plivo's WhatsApp Business API lets you send programmatic messages while our AI chatbot handles customer service 24/7. Create meaningful conversations that drive results.
Learn More






Learn how our carrier network connectivity and reliability are your competitive advantage

What our customers say about us?

“Plivo's queuing system was a huge selling point. With fewer worries about rate limits and batch sizes, our developers face less burden. If we need to send 50,000 messages, we simply send them all—Plivo handles the rest, delivering without us worrying about the process.”

“Deliverability increased by 9% over our previous provider, proving Plivo's network is top-notch. Plivo is more economically viable, with a reliable network saving us wasted costs. Responsive support: The team goes out of their way to solve even very technical questions.”

“For MDabroad, Plivo has completely transformed our call quality. Our team rarely hears complaints from users or call center operators. Previously, call logs showed many drops and repeats with other carriers—now connections are solid. Plus, our costs have significantly decreased.”

“Our developers engaged with Plivo's technical team, reviewed documentation, and compared providers—concluding Plivo met all our needs. Things have been smoother with them. Even as a low-volume user, they treat us as essential, which really matters to us.”

“Using Plivo and using SMS gives customers an easy way to communicate with us. If anything goes wrong we'd have thousands of people standing in a parking lot trying to pay, so it's mission-critical for us. We're very happy with Plivo. The price is better too.”

“Plivo empowers us to operate in over 190 countries—a major advantage as political parties worldwide use voice to reach voters. CallHub thrives on Plivo's global carrier ties. Each call becomes a well-orchestrated API sequence, relying on Plivo’s highly available, scalable, and latency-free Voice API cycles.”

“Plivo's queuing system was a huge selling point. With fewer worries about rate limits and batch sizes, our developers face less burden. If we need to send 50,000 messages, we simply send them all—Plivo handles the rest, delivering without us worrying about the process.”

“Deliverability increased by 9% over our previous provider, proving Plivo's network is top-notch. Plivo is more economically viable, with a reliable network saving us wasted costs. Responsive support: The team goes out of their way to solve even very technical questions.”

“For MDabroad, Plivo has completely transformed our call quality. Our team rarely hears complaints from users or call center operators. Previously, call logs showed many drops and repeats with other carriers—now connections are solid. Plus, our costs have significantly decreased.”

“Our developers engaged with Plivo's technical team, reviewed documentation, and compared providers—concluding Plivo met all our needs. Things have been smoother with them. Even as a low-volume user, they treat us as essential, which really matters to us.”

“Using Plivo and using SMS gives customers an easy way to communicate with us. If anything goes wrong we'd have thousands of people standing in a parking lot trying to pay, so it's mission-critical for us. We're very happy with Plivo. The price is better too.”

“Plivo empowers us to operate in over 190 countries—a major advantage as political parties worldwide use voice to reach voters. CallHub thrives on Plivo's global carrier ties. Each call becomes a well-orchestrated API sequence, relying on Plivo’s highly available, scalable, and latency-free Voice API cycles.”

“Plivo's queuing system was a huge selling point. With fewer worries about rate limits and batch sizes, our developers face less burden. If we need to send 50,000 messages, we simply send them all—Plivo handles the rest, delivering without us worrying about the process.”

“Deliverability increased by 9% over our previous provider, proving Plivo's network is top-notch. Plivo is more economically viable, with a reliable network saving us wasted costs. Responsive support: The team goes out of their way to solve even very technical questions.”

“For MDabroad, Plivo has completely transformed our call quality. Our team rarely hears complaints from users or call center operators. Previously, call logs showed many drops and repeats with other carriers—now connections are solid. Plus, our costs have significantly decreased.”

“Our developers engaged with Plivo's technical team, reviewed documentation, and compared providers—concluding Plivo met all our needs. Things have been smoother with them. Even as a low-volume user, they treat us as essential, which really matters to us.”

“Using Plivo and using SMS gives customers an easy way to communicate with us. If anything goes wrong we'd have thousands of people standing in a parking lot trying to pay, so it's mission-critical for us. We're very happy with Plivo. The price is better too.”

“Plivo empowers us to operate in over 190 countries—a major advantage as political parties worldwide use voice to reach voters. CallHub thrives on Plivo's global carrier ties. Each call becomes a well-orchestrated API sequence, relying on Plivo’s highly available, scalable, and latency-free Voice API cycles.”
Two ways to get started with Plivo
Create your Plivo account or contact sales to discuss volume discounts starting at $1000/month








.webp)